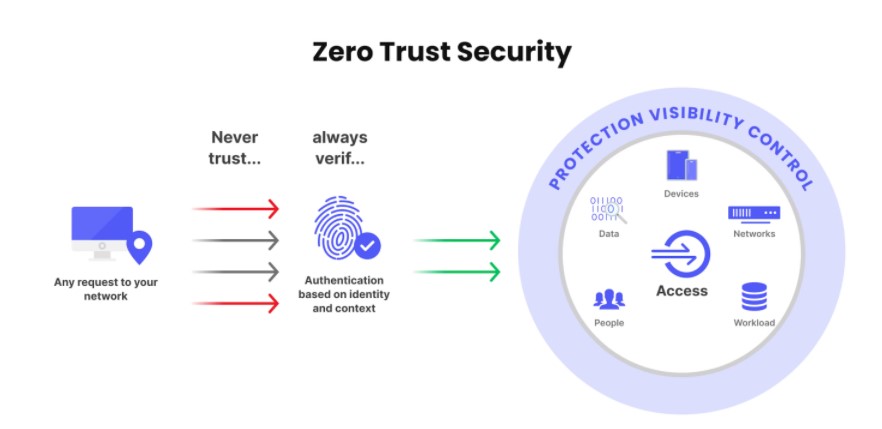
Insider Threats Representation: Draw conceptualizations that shed the difference between insiders’ and outsiders’ attack profiles. Insider threats are originator challenges since they usually direct access through appropriate human agents to the sensitive system and data resources. They may be dubious individuals, negligent employees, or compromised insiders whose credential is abused by an external attacker. The traditional security model does not often deploy perimeter defensive mechanisms that usually provide discharges from the detection and prevention of such threats. The Zero Trust Security, though, with its philosophy that “never trust, always verify,” forms a strong paradigm in turning end-users into customers or even mitigating against insider threats through tight access control, continuous monitoring, and finite data protection.
Insider threats are very risky because the insiders bypass most of the point controls that protect against external threats. They usually misuse their access privileges purposely or by accident to leak sensitive data, disrupt business processes, or alter or destroy systems. Towards this end, it has been aggravated by expanding remote working, cloud adoption, and increasing complexity within IT environments. Hence, the gap has widened over time into posing an amplified risk of insider threats.
Zero Trust Security addresses threats from within the organization with certain principles and practices:
1. Why Implicit Trust Must Go
No user, device, or application is given trust merely for being inside the network. In fact, the Zero Trust Security is particularly effective in addressing insider threats, as all access requests are treated with equal scrutiny irrespective of the source, in line with no trust philosophy.
2. Granular Access Control and Least Privilege
In line with the previous tenets, Zero Trust Security retains the idea of least privilege, with access to any resource being granted only to the users and devices that strictly need it to complete specified tasks. In this case, the operator is not able to sabotage the system by accessing non-critical or highly sensitive information.
3. Behavioural Analytics Adding Continuous Monitoring
It identifies apps as they dynamically access resources while checking every request activity against parameters including identity, device health, location, and user behavior patterns? This is how Zero Trust Security assesses all requests against “human” analysis while constantly monitoring.
4. Micro-segmentation
Zero Trust has micro-segmentation, creating zones in a network and isolating each from one another through its access control, preventing lateral movement within the network in both cases.
5. Real-Time Threat Detection and Response
To thwart any potential insider threats, Zero Trust Security comprises mechanisms for real-time detecting threats and continuous monitoring. In this way, when any dubious activities take place, such as bringing an account to the lockout or freezing access, the very detection, and response is undertaken either through machine learning or artificial intelligence, in real-time.
Notification of Implementation of Zero Trust Security for Insider Threats
Performing the implementation of Zero Trust Security shall gives the following for the organization:
Less risk: Access on sensitive systems is thus restricted, and cumbersome tracking is established in order to neutralize insider threats.
Advanced detection: Real-time anomaly detection helps to minimize opportunities for unnoticed breaches.
Conclusion
While traditional security models leave organizations vulnerable to internal threats, Zero Trust goes further in considering and treating unique problems posed by malign, negligent, or even compromised users. Zero Trust provides the unique defense mechanism against insider threats and thereby shields organizations’ critical assets in the long run, while strengthening their resilience.